Issue setting up Lookup Service in NSX Manager 6.4.4
Apr 21, 2019 · CommentsVMWare
Issue
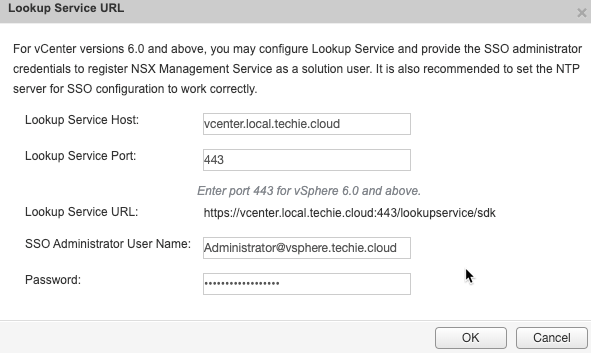
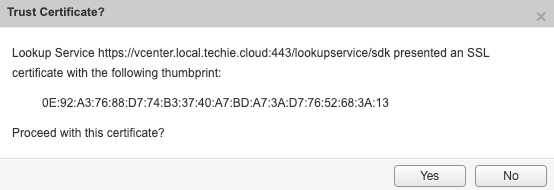
When setting up Lookup Service in NSX Manager 6.4.4 Build 11197766 I received the following error.
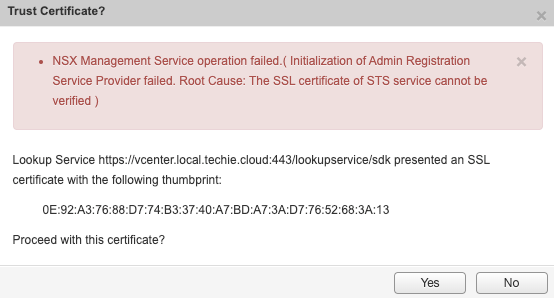
NSX Management Service operation failed.( Initialization of Admin Registration Service Provider failed. Root Cause: The SSL certificate of STS service cannot be verified )And after cancelling the status is as follows.
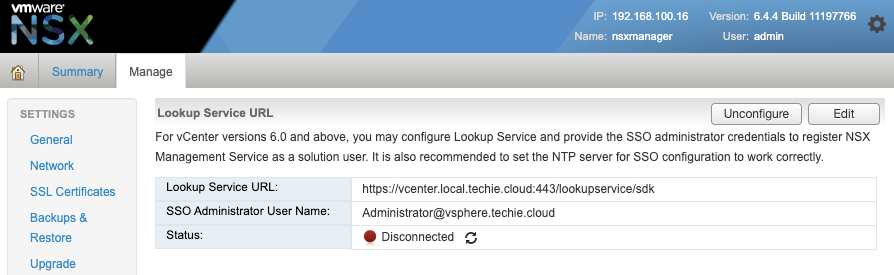
Cause of the issue
The reason for this issue is that I’ve set up vCenter with a custom SSL certificate from Buypass, while some of the other services in vCenter and the integrated PSC still uses the pre-assigned certificate created during install. To solve this we’ll need to switch the SSL certificate used by the Lookup Service also.
Fixing the issue
First you’ll need to login to your vCenter appliance with ssh.
➜ ~ ssh vcenter.local.techie.cloud -l root
VMware vCenter Server Appliance 6.7.0.30000
Type: vCenter Server with an embedded Platform Services Controller
root@vcenter.local.techie.cloud's password:
X11 forwarding request failed on channel 0
root@vcenter [ ~ ]#I’ve changed to that it automatically drops into shell, but if you have not you first will have to switch to shell by running these commands.
shell.set --enabled true
shellThe run the following command to check the SSL certificate currently in use for Lookup Service.
/usr/lib/vmidentity/tools/scripts/lstool.py list --url https://localhost/lookupservice/sdk --no-check-cert --ep-type com.vmware.cis.cs.identity.ssoThis will give an output similar to this.
Picked up JAVA_TOOL_OPTIONS: -Xms32M -Xmx128M
2019-04-21 20:38:45,653 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@38cccef: startup date [Sun Apr 21 20:38:45 CEST 2019]; root of context hierarchy
2019-04-21 20:38:45,755 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/vmodl/context_v2.xml]
2019-04-21 20:38:46,029 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@38cccef: startup date [Sun Apr 21 20:38:45 CEST 2019]; root of context hierarchy
2019-04-21 20:38:46,032 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.vmodl loaded in 454 millis
2019-04-21 20:38:46,033 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@2df32bf7: startup date [Sun Apr 21 20:38:46 CEST 2019]; root of context hierarchy
2019-04-21 20:38:46,033 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/vmodl/context_v2.xml]
2019-04-21 20:38:46,063 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@2df32bf7: startup date [Sun Apr 21 20:38:46 CEST 2019]; root of context hierarchy
2019-04-21 20:38:46,064 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.vmodl loaded in 30 millis
2019-04-21 20:38:46,064 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@1442d7b5: startup date [Sun Apr 21 20:38:46 CEST 2019]; root of context hierarchy
2019-04-21 20:38:46,064 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/lookup/context.xml]
2019-04-21 20:38:46,146 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@1442d7b5: startup date [Sun Apr 21 20:38:46 CEST 2019]; root of context hierarchy
2019-04-21 20:38:46,146 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.lookup loaded in 82 millis
2019-04-21 20:38:46,759 INFO com.vmware.vim.lookup.client.SiteAffinityServerEndpointProvider - Site affinity is disabled
2019-04-21 20:38:47,536 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Shutting down the connection monitor.
2019-04-21 20:38:47,536 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Interrupted, no more connection pool cleanups will be performed.
Service Product: com.vmware.cis
Service Type: cs.identity
Service ID: 5c12038b-47e9-4a07-84c8-6525fe4e1f71
Site ID: default-site
Owner ID: vcenter.local.techie.cloud@vsphere.techie.cloud
Version: 2.0
Endpoints:
Type: com.vmware.cis.cs.identity.sso
Protocol: wsTrust
URL: https://vcenter.local.techie.cloud/sts/STSService/vsphere.techie.cloud
SSL trust: MIIEIjCCAwqgAwIBAgIJANd5Z+LRZthMMA0GCSqGSIb3DQEBCwUAMIGoMQswCQYDVQQDDAJDQTEX
MBUGCgmSJomT8ixkARkWB3ZzcGhlcmUxHDAaBgoJkiaJk/IsZAEZFgx0ZWNoaWUuY2xvdWQxCzAJ
BgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlhMSMwIQYDVQQKDBp2Y2VudGVyLmxvY2FsLnRl
Y2hpZS5jbG91ZDEbMBkGA1UECwwSVk13YXJlIEVuZ2luZWVyaW5nMB4XDTE4MTIyODExMDMyOVoX
DTI4MTIyMjExMDMyOFowMjEjMCEGA1UEAwwadmNlbnRlci5sb2NhbC50ZWNoaWUuY2xvdWQxCzAJ
BgNVBAYTAlVTMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4tBasV9o24hAUD97+7bU
Q4MiuYz3vyTwFNzP6mLNhaPbG5GfjRZQPiFg+ROOob4k0LOhcIQmgdLgkzdDyJwuDkt3189uifR6
RvazJ7vFvaptGfr3J6dyr6Zokemu31CUisJKUHe55obsN8wNY2kH1Bn2R0a1AEQUV0NuPKkh+Yqn
y5DOh5Nv/o5r0bWBVJyI7t++ZradYqXrXdRG4Jv0TJRqKF5fODXaK3fIg4InGCRTPS0L988xax4F
Za1VXVUmYIx4t7VA77wzCL5GFmlX2y1IAVbtQnBCj7HehTKITRVX7c3MkC904P23g1rhy/djMlLG
DjuJHmvS99RQ1UFrlQIDAQABo4HDMIHAMAsGA1UdDwQEAwIDqDAlBgNVHREEHjAcghp2Y2VudGVy
LmxvY2FsLnRlY2hpZS5jbG91ZDAdBgNVHQ4EFgQUohFIn+QOjhfO0Arv+wOULUHy06swHwYDVR0j
BBgwFoAUkNKVpSO28nrkakOuV2AZrkZfLqkwSgYIKwYBBQUHAQEEPjA8MDoGCCsGAQUFBzAChi5o
dHRwczovL3ZjZW50ZXIubG9jYWwudGVjaGllLmNsb3VkL2FmZC92ZWNzL2NhMA0GCSqGSIb3DQEB
CwUAA4IBAQA03o+TuBZz7s77GXpSGleDdi3RNiSnZzyesgVSyMXrDcQgnOqYmD6QxmV43m4msjkS
sW5IExlW0dsYwHlgmIqueIbRe7B4lX2fXDywXRd2eGnIeAzldBZOfeCRRpE8kgCHgNVFpwAdfZu3
QVJmjJ3wZe8vjNZDKU2vHk9isTsePI585MbXEldXOnIqCAXlW63vDNyRDKFT5jTMRVtZ0icSToBf
+gn4Iif1OiEI4Q8nXgg94uFtNcqeACpV5KI5/w/7RAvXDrrGwaa809xYyZacihNIj417pnwemOqW
vNSMK/uOYHUZbzh0LXjTSDqE8YBGP2RsyNS2KcmzW5yUt8U5From this output save the textlines from ‘SSL trust:’ to notepad or your favourite text editor. Then run the following command.
echo | openssl s_client -connect localhost:443This will give out similar of this.
CONNECTED(00000003)
depth=2 C = NO, O = Buypass AS-983163327, CN = Buypass Class 2 Root CA
verify return:1
depth=1 C = NO, O = Buypass AS-983163327, CN = Buypass Class 2 CA 5
verify return:1
depth=0
verify return:1
---
Certificate chain
0 s:
i:/C=NO/O=Buypass AS-983163327/CN=Buypass Class 2 CA 5
1 s:/C=NO/O=Buypass AS-983163327/CN=Buypass Class 2 CA 5
i:/C=NO/O=Buypass AS-983163327/CN=Buypass Class 2 Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIGSjCCBDKgAwIBAgIKCUpunDMlC/ymNTANBgkqhkiG9w0BAQsFADBLMQswCQYD
VQQGEwJOTzEdMBsGA1UECgwUQnV5cGFzcyBBUy05ODMxNjMzMjcxHTAbBgNVBAMM
FEJ1eXBhc3MgQ2xhc3MgMiBDQSA1MB4XDTE5MDEwNDE5MDEyNFoXDTE5MDcwMzIx
NTkwMFowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKvhS3/ubjqC
zt6G9TrFOR21XAgtnCkvpSSMvV7OAi2KOEy0LZm+Gzsz9Gz76P2X6/3JCRLdLq8j
WyjeyAK/LSeYcGQc6TTCTPqubWf57EN0qfC6V/wGHzAXCPX9zN097PMnTogqGrI3
gI85aTqjSTJiz5PKDQzhQxgyh3Ew0SD2E8/S8kMzIBN1U808BVwPep6StDpF9dFj
GzcArthBdwkMs5t3ocvQTFtoFAnv2P8cAMHqqSWsv8iWKX7gPJWQP8NFhdDQJ35x
RLM1Hltj2rqyx2CMHbX1JKHDcMOMm9YDoGDuLZac3V86fe0ghg/pVHmmtvb9kkbe
VuRXjdtAHzcCAwEAAaOCAnkwggJ1MAkGA1UdEwQCMAAwHwYDVR0jBBgwFoAUJ1Kk
by0qq0CTkOzWacv+fGE7fEIwHQYDVR0OBBYEFC7y0NSXvQOWJ0V6IQKryvd3Ao23
MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
HwYDVR0gBBgwFjAKBghghEIBGgECBzAIBgZngQwBAgEwOgYDVR0fBDMwMTAvoC2g
K4YpaHR0cDovL2NybC5idXlwYXNzLm5vL2NybC9CUENsYXNzMkNBNS5jcmwwKAYD
VR0RAQH/BB4wHIIadmNlbnRlci5sb2NhbC50ZWNoaWUuY2xvdWQwagYIKwYBBQUH
AQEEXjBcMCMGCCsGAQUFBzABhhdodHRwOi8vb2NzcC5idXlwYXNzLmNvbTA1Bggr
BgEFBQcwAoYpaHR0cDovL2NydC5idXlwYXNzLm5vL2NydC9CUENsYXNzMkNBNS5j
ZXIwggEEBgorBgEEAdZ5AgQCBIH1BIHyAPAAdgC72d+8H4pxtZOUI5eqkntHOFeV
CqtS6BqQlmQ2jh7RhQAAAWgaPdHFAAAEAwBHMEUCIQDNPD9nD7HY3zf7QDfu2NyA
GZemRhfCegVvXCTCdjw7owIga/RJ5M92+G87fBC56UYu76q1vsi3PppAcZEMHkjC
jDsAdgBVgdTCFpA2AUrqC5tXPFPwwOQ4eHAlCBcvo6odBxPTDAAAAWgaPdMsAAAE
AwBHMEUCIQDQ6f/56ATbSTOWYO7ON04Je6ep4U0TEJPKausqRYteSQIgICerCEom
qEYG0TzUdNWvvEQCJvtccB/5T8bIJwuVsBMwDQYJKoZIhvcNAQELBQADggIBAA5B
6Bfca3q2i4N2POnDk86IH62JVqPfh/n7AKABI+gOCAx+ChJ08WKkK42FOt2ajZ7i
scE0rxxm8CVFuo/zGC+DcLlbKEqsGMw5Km3wKEFG65d44TxgmFqkyReyV6TfcQM6
krUUOtWOHdcSMfdkfe2cKantlBbC4r8DaOQ6/Ptif4rDCE1MTB4hBVWnbh9xZp5d
5Y7P54rwhwLlkZyA0chwT1KaUzUUSr0Wly+KPfH4zm0SpHfdztTguiqfj6s84kCw
0nSPhWPgR1Oq8Bw1P0Z7RUzlS9+IvVAqYARi5HjQpwUdDDIQNgvgwQD8HeEyI+YN
sqAixSxhjph3ZXERs7+5D+zzSTFno+ztEc362w/GASWWgKXboICBJJLCYQ/m8uZH
2q9meggFrzCNgR+jcM13Q5ITa6g8CTE9Lf8RxhG/0SepdyPAsniBiG9IxzkG86L1
TPrP8APRj7XgpENtbtSYZY7LeytvIfxaOpcezoM80nz8IqUbTFVoSB1yr+2/jQb4
3HDUp5EUf/8Vkbo9e22YPSd3Dr1qovOdGthEHSZ57yhj8nr031eQR2Jl3gRzDrGm
Lwd3AMewwrs4fk0HyR8CwvupbG4fotK+PNHlNFlJ0RWbYkDgPc9MgHoKChe2wRvy
eVovg0calEfdHPCetTTmbfgvo7NCj0KVAlCwCyNa
-----END CERTIFICATE-----
subject=
issuer=/C=NO/O=Buypass AS-983163327/CN=Buypass Class 2 CA 5
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 3659 bytes and written 433 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID:
Session-ID-ctx:
Master-Key: F4A8B4356E66BC2394E07E9E55EE1620E740082F876BD2A4BB0126B9CF22806A516EEBD5E6736612D9B00BB578459359
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1555871987
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
DONEFrom this output you can compare tthe text lines between ‘—–BEGIN CERTIFICATE—–’ and ‘—–END CERTIFICATE—–’, with the text lines from ‘SSL trust:’ that you saved in a text editor earlier. If these lines differ then you have the same issue as me, and will need to switch the SSL certificate in use for Lookup Service.
You can then continue with the following commands. You’ll need to insert the text lines saved in your favourite text editor between ‘—–BEGIN CERTIFICATE—–’ and ‘—–END CERTIFICATE—–’ in the commands below.
mkdir /certificate
cd /certificate
cat <<'EOF' >> /certificate/old_lookup_cert.cert
-----BEGIN CERTIFICATE-----
MIIEIjCCAwqgAwIBAgIJANd5Z+LRZthMMA0GCSqGSIb3DQEBCwUAMIGoMQswCQYDVQQDDAJDQTEX
MBUGCgmSJomT8ixkARkWB3ZzcGhlcmUxHDAaBgoJkiaJk/IsZAEZFgx0ZWNoaWUuY2xvdWQxCzAJ
BgNVBAYTAlVTMRMwEQYDVQQIDApDYWxpZm9ybmlhMSMwIQYDVQQKDBp2Y2VudGVyLmxvY2FsLnRl
Y2hpZS5jbG91ZDEbMBkGA1UECwwSVk13YXJlIEVuZ2luZWVyaW5nMB4XDTE4MTIyODExMDMyOVoX
DTI4MTIyMjExMDMyOFowMjEjMCEGA1UEAwwadmNlbnRlci5sb2NhbC50ZWNoaWUuY2xvdWQxCzAJ
BgNVBAYTAlVTMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4tBasV9o24hAUD97+7bU
Q4MiuYz3vyTwFNzP6mLNhaPbG5GfjRZQPiFg+ROOob4k0LOhcIQmgdLgkzdDyJwuDkt3189uifR6
RvazJ7vFvaptGfr3J6dyr6Zokemu31CUisJKUHe55obsN8wNY2kH1Bn2R0a1AEQUV0NuPKkh+Yqn
y5DOh5Nv/o5r0bWBVJyI7t++ZradYqXrXdRG4Jv0TJRqKF5fODXaK3fIg4InGCRTPS0L988xax4F
Za1VXVUmYIx4t7VA77wzCL5GFmlX2y1IAVbtQnBCj7HehTKITRVX7c3MkC904P23g1rhy/djMlLG
DjuJHmvS99RQ1UFrlQIDAQABo4HDMIHAMAsGA1UdDwQEAwIDqDAlBgNVHREEHjAcghp2Y2VudGVy
LmxvY2FsLnRlY2hpZS5jbG91ZDAdBgNVHQ4EFgQUohFIn+QOjhfO0Arv+wOULUHy06swHwYDVR0j
BBgwFoAUkNKVpSO28nrkakOuV2AZrkZfLqkwSgYIKwYBBQUHAQEEPjA8MDoGCCsGAQUFBzAChi5o
dHRwczovL3ZjZW50ZXIubG9jYWwudGVjaGllLmNsb3VkL2FmZC92ZWNzL2NhMA0GCSqGSIb3DQEB
CwUAA4IBAQA03o+TuBZz7s77GXpSGleDdi3RNiSnZzyesgVSyMXrDcQgnOqYmD6QxmV43m4msjkS
sW5IExlW0dsYwHlgmIqueIbRe7B4lX2fXDywXRd2eGnIeAzldBZOfeCRRpE8kgCHgNVFpwAdfZu3
QVJmjJ3wZe8vjNZDKU2vHk9isTsePI585MbXEldXOnIqCAXlW63vDNyRDKFT5jTMRVtZ0icSToBf
+gn4Iif1OiEI4Q8nXgg94uFtNcqeACpV5KI5/w/7RAvXDrrGwaa809xYyZacihNIj417pnwemOqW
vNSMK/uOYHUZbzh0LXjTSDqE8YBGP2RsyNS2KcmzW5yUt8U5
-----END CERTIFICATE-----
EOFThen you can use the following commands to first save the SSL certificate currently in use for port 443 on vCenter, and then get the SHA1 fingerprint of the old one in use for Lookup Service. These will be used in later commands.
/usr/lib/vmware-vmafd/bin/vecs-cli entry getcert --store MACHINE_SSL_CERT --alias __MACHINE_CERT --output /certificate/new_machine.cert
openssl x509 -in /certificate/old_lookup_cert.cert -noout -sha1 -fingerprintThe last command will give an outpout similar to.
SHA1 Fingerprint=F9:81:93:65:A5:69:40:ED:A3:B1:2D:B2:1C:97:A2:57:CD:A8:BB:47Then we’ll use the previous information to update the SSL certificate information for Lookup Service. You’ll need to replace user parameter with your own username, and password parameter with your own password in the command.
cd /usr/lib/vmidentity/tools/scripts/
python ls_update_certs.py --url https://vcenter.local.techie.cloud/lookupservice/sdk --fingerprint F9:81:93:65:A5:69:40:ED:A3:B1:2D:B2:1C:97:A2:57:CD:A8:BB:47 --certfile /certificate/new_machine.cert --user Administrator@vsphere.techie.cloud --password passwordThe command will take a while, and will give the following output.
Get site name
Picked up JAVA_TOOL_OPTIONS: -Xms32M -Xmx128M
...<SNIPPED OUT 1000 lines of log>...
2019-04-21 20:58:07,547 INFO com.vmware.identity.token.impl.SamlTokenImpl - SAML token for SubjectNameId [value=Administrator@VSPHERE.TECHIE.CLOUD, format=http://schemas.xmlsoap.org/claims/UPN] successfully parsed from Element
2019-04-21 20:58:07,584 INFO com.vmware.vim.sso.client.impl.SecurityTokenServiceImpl - Successfully acquired token for user: Administrator@vsphere.techie.cloud
2019-04-21 20:58:07,586 INFO com.vmware.vim.lookup.client.SiteAffinityServerEndpointProvider - Site affinity is disabled
2019-04-21 20:58:07,807 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Shutting down the connection monitor.
2019-04-21 20:58:07,808 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Interrupted, no more connection pool cleanups will be performed.
Get service 62eff35e-00f0-4da4-88a6-3a1ebd5d1775
Picked up JAVA_TOOL_OPTIONS: -Xms32M -Xmx128M
2019-04-21 20:58:08,106 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@57fa26b7: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,170 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/vmodl/context_v2.xml]
2019-04-21 20:58:08,405 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@57fa26b7: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,408 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.vmodl loaded in 335 millis
2019-04-21 20:58:08,409 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@2bea5ab4: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,409 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/vmodl/context_v2.xml]
2019-04-21 20:58:08,436 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@2bea5ab4: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,437 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.vmodl loaded in 27 millis
2019-04-21 20:58:08,438 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Refreshing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@32464a14: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,438 INFO org.springframework.beans.factory.xml.XmlBeanDefinitionReader - Loading XML bean definitions from class path resource [com/vmware/vim/binding/lookup/context.xml]
2019-04-21 20:58:08,523 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext - Closing com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl$NonValidatingClassPathXmlApplicationContext@32464a14: startup date [Sun Apr 21 20:58:08 CEST 2019]; root of context hierarchy
2019-04-21 20:58:08,524 INFO com.vmware.vim.vmomi.core.types.impl.VmodlContextImpl - Package com.vmware.vim.binding.lookup loaded in 85 millis
2019-04-21 20:58:08,986 INFO com.vmware.vim.lookup.client.SiteAffinityServerEndpointProvider - Site affinity is disabled
2019-04-21 20:58:09,325 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Shutting down the connection monitor.
2019-04-21 20:58:09,325 WARN com.vmware.vim.vmomi.client.http.impl.HttpConfigurationCompilerBase$ConnectionMonitorThreadBase - Interrupted, no more connection pool cleanups will be performed.
Don't update service 62eff35e-00f0-4da4-88a6-3a1ebd5d1775
Updated 31 service(s)As can be seen by the last line ‘Updated 31 service(s)’, it was a success! We can now continue to set up the Lookup Service in NSX Manager.