Mitigating concurrent-context attack vector on VMWare 6.7
Apr 20, 2019 · CommentsVMWare
Issue
VMWare reports an health issue regarding concurrent-context attack vector, which you can read more details about at TinkerTry and also at VMWare KB55806 and KB55767.
And in vSphere Web GUI it will show an warning like this.
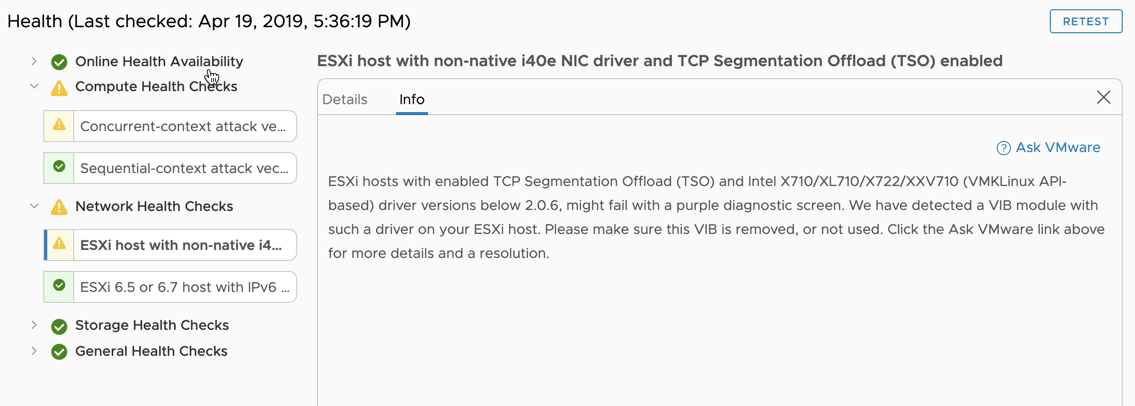
Fixing the issue
Two measures of fixing the issue is described at VMWare KB55806. Now the pre-requisite for fixing this is of course that both your vCenter and ESXi servers are patched and up to date.
To fix the issue one would need to change to one of two new schedulers, either ESXI Side-Channel-Aware Scheduler which is available in ESXi 5.5, 6.0, 6.5, and 6.7 prior to 6.7u2, or ESXi Side-Channel-Aware Scheduler v2 which is available in ESXi 6.7 Update 2 and later.
Changing the sceduler to remediate the issue will most likely give an performance hit on your environment, so plan accordingly. VMWare also has an whitepaper about the schedulers located here.
Changing the scheduler in 6.7u2
To change the scheduler in 6.7 Update 2 Web GUI log in to your environment. Then select one of your hosts, and choose ‘Configure’.
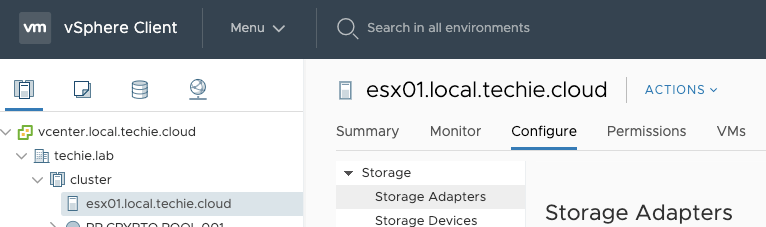
Then choose ‘Advanced System Settings’.
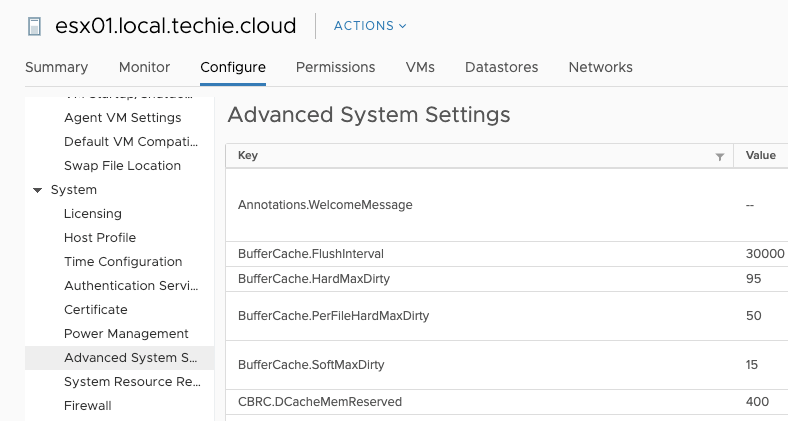
Then press the button ‘Edit’, and filter for ‘hyperthreadingMitigation’. To change to the new scheduler in VMWare 6.7 Update 2 you need to change the value of ‘VMkernel.Boot.hyperthreadingMitigation’ to ’true’ and ‘VMkernel.Boot.hyperthreadingMitigationIntraVM’ to ‘false’, and the press ‘OK’.
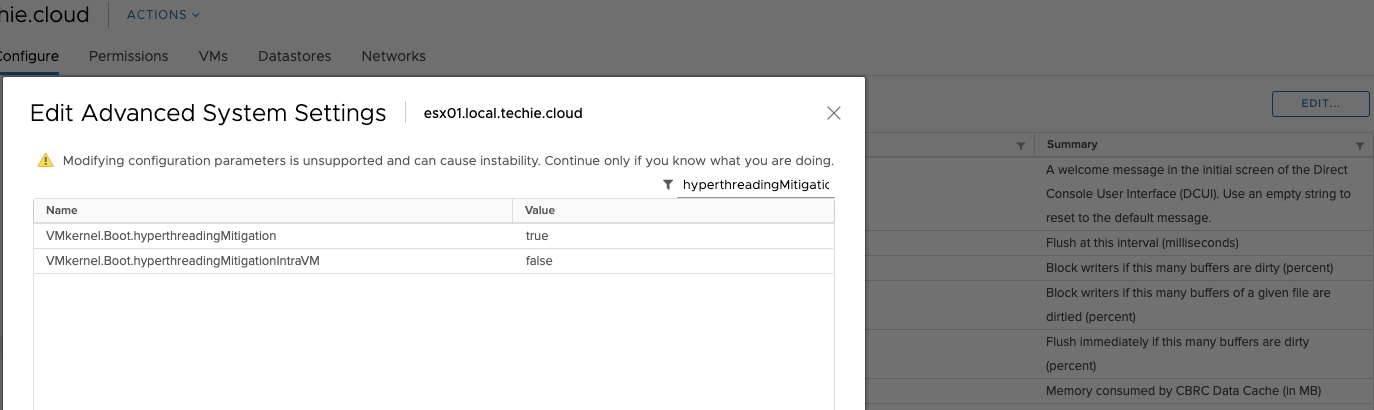
After those values has been set, you’ll need to reboot your ESXi server to enable the new setting.