Using 3rd party generated certificate and private key on EM12c
Oct 29, 2013 · CommentsOracle
This will show you how to use an existing certificate and private key and use it on the Cloud Control 12c web console. First copy the certificate and private key to a folder on the server. You should have similar files to this
star_idontknowthis_com.cert #The certificate in pem format
star_idontknowthis_com.key #The key in pem format
cacerts.cert #File containing all the root and intermediate certificates in pem formatThen run the command
openssl pkcs12 -export -in star_idontknowthis_com.cert -inkey star_idontknowthis_com.key -certfile cacerts.cert -out ewallet.p12You now have to type the password of the private key if you have one. And also make sure to set a new export password. This will give you an output file of “ewallet.p12”.
Now run Oracle Wallet Manager
$MW_HOME/Oracle_WT/bin/owm
NB! Don’t run Oracle Wallet Manager from the Oracle Database home as that might give you following error message in the logfile
2013-10-28 10:38:09,658 [main] ERROR oms.SecureConsoleCmds main.178 - Failed to secure the Console: PKI-02002: Unable to open the wallet. Check password.EOF
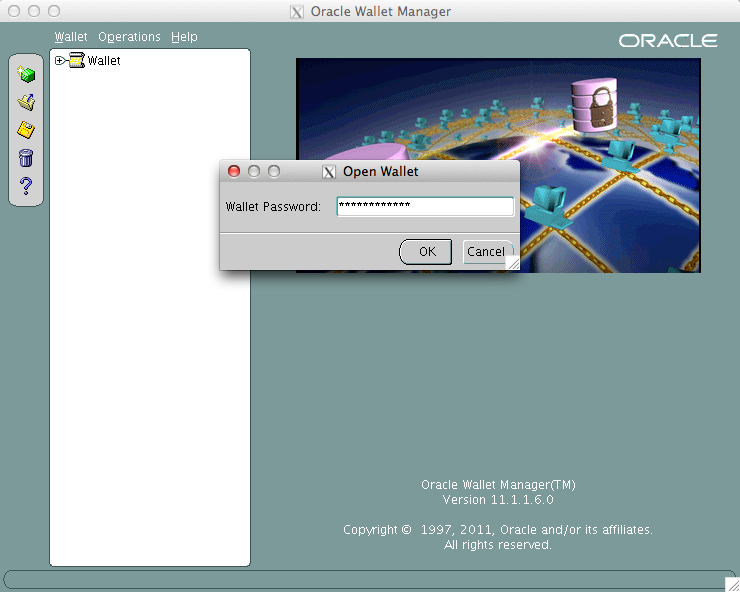
Now open the folder with the “ewallet.p12” file created earlier.

And then enter the export password you entered earlier
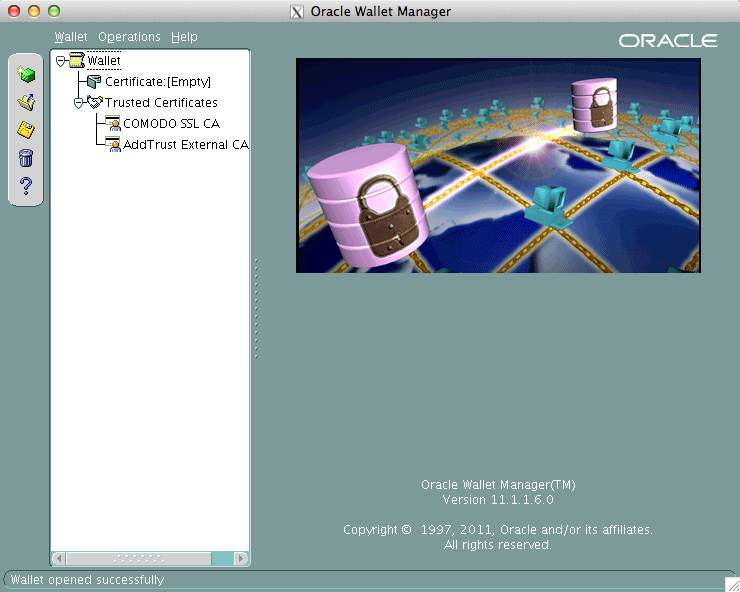
Now it will look similar to this
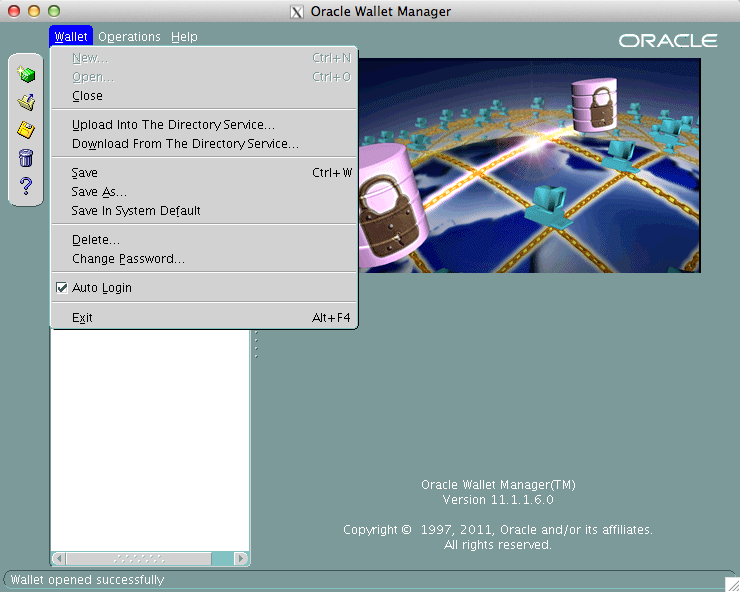
Then you need to go to “Wallet” and check the box in front of “Auto Login”.
The exit Oracle Wallet Manager. Now to import the certificate to Cloud Control.
$MW_HOME/oms/bin/emctl stop oms -all
$MW_HOME/oms/bin/emctl secure console -wallet /home/oracle/SSL/This should give you a message that the command succeeded. If it failed you should check the log file “$MW_HOME/../gc_inst/em/EMGC_OMS1/sysman/log/secure.log” for errors.
If it succeeded you can now start up OMS again and you should be up and running with a new certificate.
$MW_HOME/oms/bin/emctl start oms